Automate. Hunt. Defend.
For Operators. By Operators.

Autonomous & Agentic Defense
An AI-native, edge-deployed cyber defense platform that autonomously detects, validates, and responds to real threats on the wire. Built for environments where cloud-based tools and human-scaled workflows fail.
Autonomous Threat Detection
Analyzes live network traffic using operator-trained AI to identify adversary behavior directly from internal communications. Detection is behavioral, not signature- or baseline-driven, enabling discovery of advanced and unknown threats in real time.
Agentic Defense & Response
Executes a complete autonomous defense loop, from detection and validation to intelligence reporting and remediation. Decisions occur at machine speed, eliminating dependence on manual triage and analyst intervention.
Mission-Flexible Deployment
Operates fully on-prem and in air-gapped environments with no required cloud dependencies, while supporting hybrid or cloud-connected deployments as needed. Delivers consistent autonomous defense across IT, OT, and critical infrastructure without loss of control or performance.

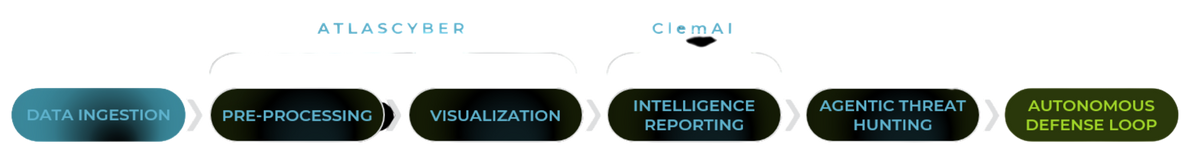
How it works
Autonomous & Real Threat Hunting at The Edge
-
CrunchAtlas passively collects PCAP, NetFlow, or CSV’s securely from customer networks, either on premises or remotely, either with our CrunchSense sensor (NBR), or manually uploaded via our API or web interface.
-
CrunchAtlas’s Graphite engine analyzes traffic in seconds, identifying threats on the wire in near real-time, which are derived from internal network communication behavior. No cloud feeds required.
-
Using ClemAI, our in-house fine tuned, and developed edge-based AI, the platform will agentically analyzes and displays chosen threat cases leveraging ingested metadata and network capture, mapping findings to the MITRE ATT&CK framework autonomously and at scale.
-
ClemAI compiles findings into structured intelligence reports with severity scoring, attack context, and IOCs if true positives are confirmed.
Reports can be exported or used to power an agentic hunt, all processed on-prem, from within the platform. No external processing required. -
Built-in automated workflows re-evaluate data, vulnerability scan, react and remediate. This loop enables true autonomous detection and remediation, fueling an effective active cyber defense cycle, previously only achievable with expensive cyber expert human resources.
-
AtlasCyber transforms raw data into autonomous situational awareness, enabling air gapped and on-prem threat detection, threat hunting, and remediation measures, across OT and IT networks.